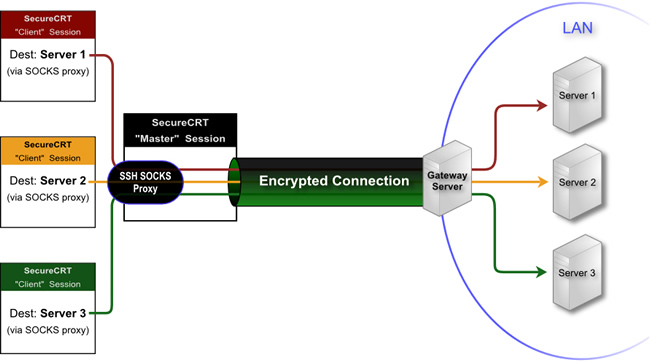
Understanding Socks Configuration: A Comprehensive Guide
In the realm of network security and internet privacy, socks configuration plays a pivotal role. Short for Socket Secure, SOCKS is an internet protocol that routes network packets between a client and server through a proxy server. This makes it possible to bypass firewalls, access geographically restricted content, and enhance online anonymity. This comprehensive guide delves into the intricacies of socks configuration, exploring its benefits, different versions, setup procedures, and potential use cases.
What is SOCKS?
SOCKS, at its core, is a proxy protocol. Unlike HTTP proxies that only handle web traffic, SOCKS proxies can handle any type of network traffic, including email, FTP, and torrents. This versatility makes socks configuration a powerful tool for various applications. The protocol operates at Layer 5 (Session Layer) of the OSI model, meaning it sits between the application layer and the transport layer.
The primary function of a SOCKS proxy is to relay traffic. When a client connects to a SOCKS proxy, it requests the proxy to establish a connection to a specific server on its behalf. All subsequent traffic between the client and server is then routed through the proxy. This process effectively masks the client’s IP address, making it appear as if the traffic is originating from the proxy server itself.
SOCKS Versions: SOCKS4 vs. SOCKS5
There are two main versions of the SOCKS protocol: SOCKS4 and SOCKS5. While both serve the same fundamental purpose, there are key differences that make SOCKS5 the more modern and widely preferred option.
SOCKS4
SOCKS4 is the older version of the protocol. It supports basic proxying functionality, including TCP connections and simple authentication. However, it has several limitations:
- No UDP Support: SOCKS4 only supports TCP connections, meaning it cannot be used for applications that rely on UDP, such as online gaming or voice over IP (VoIP).
- Limited Authentication: SOCKS4 only supports a simple form of authentication based on IP address and user ID. This makes it vulnerable to security breaches.
- No Encryption: SOCKS4 does not encrypt the traffic passing through the proxy, making it susceptible to eavesdropping.
SOCKS5
SOCKS5 addresses the limitations of SOCKS4 by offering several improvements:
- UDP Support: SOCKS5 supports both TCP and UDP connections, making it suitable for a wider range of applications.
- Multiple Authentication Methods: SOCKS5 supports various authentication methods, including username/password authentication and GSSAPI (Generic Security Services Application Programming Interface), which allows for stronger authentication.
- Encryption: While not mandatory, SOCKS5 can be used with encryption protocols like SSL/TLS to secure the traffic passing through the proxy.
- IPv6 Support: SOCKS5 supports IPv6 addresses, the latest version of the Internet Protocol, while SOCKS4 is limited to IPv4.
Due to its enhanced security features, broader compatibility, and improved performance, SOCKS5 is generally the preferred choice for socks configuration.
Benefits of Using a SOCKS Proxy
Socks configuration offers several advantages, making it a valuable tool for individuals and organizations alike:
- Bypassing Firewalls: SOCKS proxies can bypass firewalls by routing traffic through a different port or IP address. This is particularly useful for accessing websites or services that are blocked by a firewall.
- Accessing Geographically Restricted Content: By connecting to a SOCKS proxy located in a different country, users can access content that is restricted to that region. This is often used to stream videos, access news websites, or participate in online gaming.
- Enhanced Online Anonymity: SOCKS proxies mask the user’s IP address, making it more difficult to track their online activity. This is beneficial for protecting privacy and avoiding surveillance.
- Improved Security: SOCKS5 proxies, especially when used with encryption, can enhance security by protecting traffic from eavesdropping and tampering.
- Versatile Application: Unlike HTTP proxies, SOCKS proxies can handle any type of network traffic, making them suitable for a wide range of applications.
How to Configure a SOCKS Proxy
The process of socks configuration varies depending on the operating system and application being used. However, the general steps are as follows:
- Obtain SOCKS Proxy Details: You will need the IP address and port number of the SOCKS proxy server. This information is typically provided by your proxy provider or network administrator.
- Configure Your Browser: Most web browsers allow you to configure a SOCKS proxy in their settings. Look for options related to proxy servers or network settings. Enter the IP address and port number of the SOCKS proxy. You may also need to specify the SOCKS version (SOCKS4 or SOCKS5) and provide authentication credentials if required.
- Configure Your Operating System: Some operating systems allow you to configure a SOCKS proxy system-wide. This means that all applications will use the proxy by default. The configuration process varies depending on the operating system.
- Configure Specific Applications: Some applications, such as email clients or torrent clients, have their own proxy settings. You will need to configure the SOCKS proxy within the application’s settings.
- Test Your Configuration: After configuring the SOCKS proxy, it’s important to test that it’s working correctly. You can use online tools to check your IP address and verify that it’s being masked by the proxy server.
Socks Configuration: Step-by-Step Examples
Let’s look at a few specific examples of socks configuration on different platforms:
Configuring SOCKS Proxy in Mozilla Firefox
- Open Firefox and go to Options.
- Search for Network Settings.
- Click on Settings next to Configure how Firefox connects to the Internet.
- Select Manual proxy configuration.
- Enter the SOCKS host and port.
- Choose the SOCKS version (SOCKS5 is recommended).
- If required, enter your username and password.
- Click OK to save the settings.
Configuring SOCKS Proxy in Google Chrome
Chrome uses the system’s proxy settings. Therefore, you need to configure the SOCKS proxy in your operating system. Here’s how to do it on Windows:
- Open Control Panel.
- Go to Internet Options.
- Click on the Connections tab.
- Click on LAN settings.
- Check Use a proxy server for your LAN.
- Click on Advanced.
- Enter the SOCKS host and port.
- Click OK to save the settings.
Configuring SOCKS Proxy on macOS
- Open System Preferences.
- Go to Network.
- Select your network connection (e.g., Wi-Fi or Ethernet).
- Click on Advanced.
- Click on the Proxies tab.
- Check SOCKS Proxy.
- Enter the SOCKS host and port.
- Click OK to save the settings.
Use Cases for SOCKS Proxies
The versatility of socks configuration makes it applicable in numerous scenarios:
- Corporate Networks: Companies use SOCKS proxies to control and monitor employee internet access, ensuring compliance with security policies.
- Online Gaming: Gamers use SOCKS proxies to reduce latency and improve connection stability, especially when playing on servers located in different regions.
- Web Scraping: Web scrapers use SOCKS proxies to avoid IP bans and access data from websites that restrict access based on geographic location.
- Torrenting: Torrent users use SOCKS proxies to protect their identity and avoid being tracked by copyright holders.
- Bypassing Censorship: Individuals in countries with strict internet censorship use SOCKS proxies to access blocked websites and services.
- Secure File Transfer: SOCKS proxies can be used to securely transfer files between clients and servers, protecting sensitive data from eavesdropping.
Potential Risks and Considerations
While socks configuration offers several benefits, it’s important to be aware of potential risks and considerations:
- Proxy Server Reliability: The performance and reliability of your SOCKS proxy depend on the provider you choose. It’s important to select a reputable provider with a stable network infrastructure.
- Security Vulnerabilities: If the SOCKS proxy server is compromised, your traffic could be intercepted or manipulated. Choose a provider with strong security measures.
- Logging Policies: Some SOCKS proxy providers log user activity, which could compromise your privacy. Review the provider’s logging policies before using their service.
- Performance Overhead: Using a SOCKS proxy can introduce some performance overhead, as traffic needs to be routed through an additional server. This can result in slower browsing speeds.
- Compatibility Issues: Some applications may not be fully compatible with SOCKS proxies. Test your configuration thoroughly to ensure that everything is working correctly.
Choosing the Right SOCKS Proxy Provider
Selecting the right SOCKS proxy provider is crucial for ensuring optimal performance, security, and privacy. Here are some factors to consider:
- SOCKS Version: Ensure that the provider supports SOCKS5, as it offers enhanced security and broader compatibility compared to SOCKS4.
- Server Locations: Choose a provider with servers located in the regions you need to access content from.
- Speed and Bandwidth: Look for a provider with fast server speeds and unlimited bandwidth to ensure smooth browsing and streaming.
- Security Measures: Ensure that the provider has strong security measures in place to protect your data from eavesdropping and tampering.
- Logging Policies: Review the provider’s logging policies to ensure that they do not log your activity.
- Customer Support: Choose a provider with responsive customer support in case you encounter any issues.
- Pricing: Compare the pricing plans of different providers and choose one that fits your budget.
Conclusion
Socks configuration is a valuable tool for enhancing online privacy, bypassing firewalls, and accessing geographically restricted content. By understanding the intricacies of SOCKS proxies, their benefits, and potential risks, individuals and organizations can leverage this technology to improve their online experience and protect their data. Whether you’re a gamer looking to reduce latency, a journalist seeking to protect your sources, or simply someone who values online privacy, mastering socks configuration can be a significant asset. Always remember to choose a reputable proxy provider and prioritize security to ensure a safe and reliable experience. [See also: Proxy Server vs VPN: Which is Right for You?]
